Remote Access Security Best Practices |
Topic: CM528 |
The following best practices should be used in conjunction with the security standards implemented at the C-more installation site.
Methods used by those with malicious intent get more sophisticated every day. Therefore, Network Security should be considered at every C-more panel installation. Fortunately, new mitigation procedures and technology are becoming available every day.
The list below should be considered as a ‘bare minimum’ set of requirements for protection of the C-more HMI installation and the process and equipment to which it is connected.
Project Protection
Any C-more panel that will be remotely accessible should have the project saved as a Protected Project and this Protected Project should be sent to the panel. When a project is saved as a Protected Project, the project can never be edited by the C-more Programming software, and it can never be read from the panel. This means that if any network security provision fails, the project cannot be compromised by a malicious user. Safeguards should be taken to make sure there is a backup of the editable project as well as a backup of the protected project. It is recommended to create two backups for every version and store them in two separate locations. See Save Project as Protected.
Exposure of C-more TCP and UDP Port Numbers
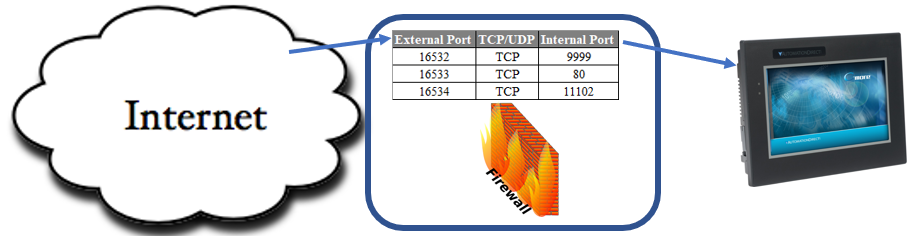
In the past, “Port Forwarding” was a common method of allowing the C-more panel applications to be accessible through a router firewall. This process is no longer recommended as it becomes a method of malicious access and exposes applications that could be otherwise protected and hidden. Today, Virtual Private Network (VPN) is a more secure method of remote accessibility.
However, if the application ports must be exposed, consider using a variety of different uncommon external port numbers that are redirected to the correct port numbers within the router's port forwarding table feature. This will make ‘finger printing’ C-more panels on the Internet very difficult.
Security Appliances
It is highly recommended to use a VPN router to remotely access any factory automation products such as C-more panels and PLC. This prevents the need for exposing application ports directly on the Internet and adds the security of creating an encrypted tunnel for any communications being sent and received. VPN technology has progressed tremendously and is readily available in a variety of form factors, including industrial hardware that can be DIN rail mounted.

Latest Firmware Version
It is always best practice to keep the C-more panel firmware up-to-date with the latest version. New means for hackers to attack networks are introduced by malicious users on a regular basis and mitigation must be added to the products to protect from these attacks. The further behind a product is on updates, the less protection the product has.
The C-more panel firmware is packaged with the software. So in order to keep the latest firmware in the C-more panel, download the latest software and use it to update the firmware in the panel.
Verify the C-more Panel Firmware Version
You must have C-more Programming Software and C-more Panel Firmware Version 2.4 or later to use Remote Access. If your panel has an earlier version of firmware, upgrade the panel firmware locally. The FAQ Help File topic section on Firmware describes how to display the panel firmware version.
If you upgrade from a version prior to Version 2.4, you must Reset to factory default using the System Setup screen on the panel after the firmware update is complete. The HTML files need to reset to add the Remote Access link.
|
|
Note: To keep your custom index file, make sure that you back up the file prior to resetting factory defaults or the index file is deleted. You cannot get it back without a back up. |
Reset the panel using the panel Setup screen.
Back up Your Custom Index File
|
|
Note: To keep your custom index file, make sure that you back up the file prior to resetting factory defaults or the index file is deleted. You cannot get it back without a back up. |
-
Save your index.htm file.
- Perform the reset to factory default.
- Copy the new index.htm file.
- Merge the functions from your custom index.htm into the newly installed index.htm with Remote Access.
Refer to the C-more Hardware User manual if you need assistance with a factory default reset.
Software Update Notifications
You can sign-up for Software update notifications at the links below:
https://support.automationdirect.com/downloads.html#notificationform
Personnel Access
Passwords for the various applications in C-more, such as FTP, HTTP and Remote Access, should only be given to trusted individuals and should be removed or changed if those individuals leave the company.
Defense in Depth
Defense in depth practices should always be used for factory automation products accessible on the Internet.
Security Considerations for Control Systems Networks
Manufacturers are realizing that to stay competitive, their Automation and Control Systems need to be more integrated within their plant. The systems often need to be integrated with upstream Enterprise Data Systems, and even further integrated to allow information to be accessible across multiple plants, or even through the Internet. This convergence of the IT world with the Automation World creates challenges in maintaining secure systems and protecting your investments in processes, personnel, Data and intellectual property.
While Automation Networks and Systems have built-in password protection schemes, this is only one very small step in securing your systems. Automation Control System Networks need to incorporate Data protection and security measures that are at least as robust as a typical business computer system. We recommend that users of PLC, HMI products and SCADA systems perform your own network security analysis to determine the proper level of security required for your application. However, the Department of Homeland Security’s National Cyber-security and Communications Integration Center (NCCIC) and Industrial Control Systems Cyber-Emergency Response Team (ICS-CERT) has provided direction related to network security and safety under an approach described as "Defense in Depth”, which is published at https://www.us-cert.gov/sites/default/files/recommended_practices/NCCIC_ICS-CERT_Defense_in_Depth_2016_S508C.pdf
This comprehensive security strategy involves physical protection methods, as well as process and policy methods. This approach creates multiple layers and levels of security for industrial automation systems. Such safeguards include the location of control system networks behind firewalls, their isolation from business networks, the use of intrusion detection systems, and the use of secure methods for remote access such as Virtual Private Networks (VPNs). Further, users should minimize network exposure for all control system devices and such control systems and these systems should not directly face the internet. Following these procedures should significantly reduce your risks both from external sources as well as internal sources, and provide a more secure system.
It is the user’s responsibility to protect such systems, just as you would protect your computer and business systems. AutomationDirect recommends using one or more of these resources in putting together a secure system:
- ICS-CERT Control Systems recommended practices at the following web address: https://ics-cert.us-cert.gov/Recommended-Practices.
- Special Publication 800-82 of the National Institute of Standards and Technology – Guide to Industrial Control Systems (ICS) Security: https://csrc.nist.gov/publications/detail/sp/800-82/rev-2/final
- ISA99, Industrial Automation and Control Systems Security https://www.isa.org/isa99/ (Tthis is a summary and these standards have to be purchased from ISA ).
The above set of resources provides a comprehensive approach to securing a control system network and reducing risk and exposure from security breaches. Given the nature of any system that accesses the internet, it is incumbent upon each user to assess the needs and requirements of their application, and take steps to mitigate the particular security risks inherent in their control system.
The latest version of the document above can be found at this link: https://support.automationdirect.com/docs/securityconsiderations.pdf
